Cloudflare recently defended against the largest-ever recorded DDoS attack, which peaked at a staggering 3.8 terabits per second (Tbps). This massive assault targeted organizations in the financial services, internet, and telecommunications sectors, using over 100 hyper-volumetric attacks to flood their systems with junk data over the course of a month. These types of attacks overwhelm the target’s network, consuming bandwidth and resources, and ultimately leaving legitimate users unable to access services.
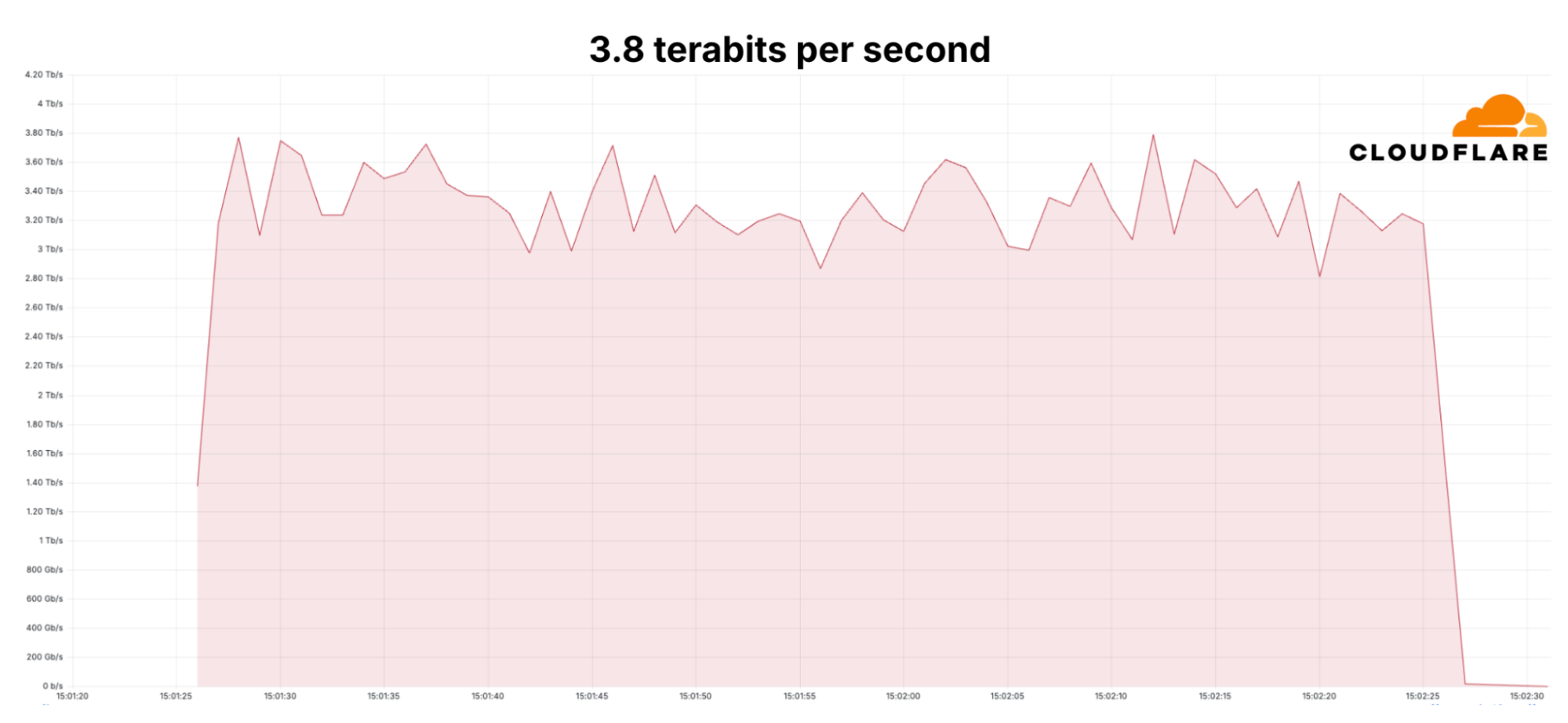
The attack affected devices across the globe, with a large concentration in Russia, Vietnam, the U.S., Brazil, and Spain. Many compromised devices included Asus home routers, MikroTik systems, DVRs, and web servers. Cloudflare, fortunately, mitigated the attack autonomously, with the largest surge lasting just 65 seconds. Using a fast but connectionless protocol called UDP, the attackers were able to bombard networks with massive data flows without establishing a formal connection, making defense even more challenging.
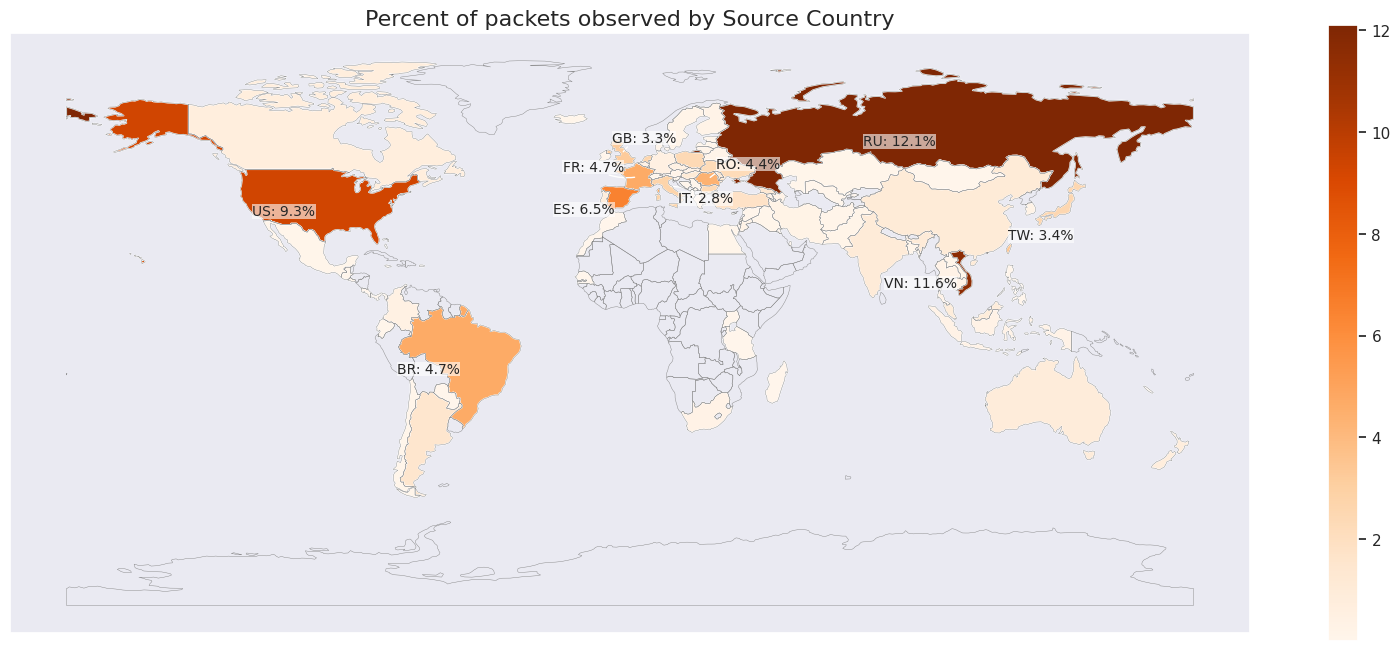
For users, this kind of disruption can mean everything from slow or inaccessible services to severe financial or operational downtime. With the rise of such large-scale attacks, it’s a clear reminder of how vulnerable our interconnected devices can be. Businesses and individuals alike need to remain vigilant, ensuring that routers, servers, and other connected devices are secured with regular updates and strong defenses.
Akamai’s report this week also raised concerns about vulnerabilities in Linux’s CUPS system, which could further amplify DDoS attacks. Their findings suggest that over 58,000 systems are at risk, with some servers capable of sending thousands of requests repeatedly in response to exploits. As cyberattacks grow in scale and complexity, the need for robust defenses has never been more urgent.